APTs are a major concern for businesses. Stay protected with our guide on the best APT detection and defense tools and software.
More...
APTs are a major source of concern for businesses of all kinds. These very sophisticated hacks are aimed to circumvent typical security measures and gain long-term illegal access to a network. As technology advances and the threat landscape gets more complicated, it is critical for enterprises to have the proper detection and defense technologies in place.
Read until the end and learn some tips to fight the threats!

Advanced persistent threats (APTs) differ from regular cyberattacks in that they are persistent, stealthy, and target specific businesses. They frequently entail numerous stages, such as reconnaissance, weaponization, distribution, exploitation, and backdoor installation.
Malware, phishing, and social engineering strategies are all examples of APTs. They are usually carried out by state-sponsored actors or well-funded criminal organizations.
Key Elements of APT Detection and Defense
APT Detection
Organizations must have visibility into all network traffic and activities in order to detect APTs. This involves keeping an eye out for signals of malicious activity, such as strange traffic patterns, aberrant behavior, and suspicious file activity.
They can benefit from APT detection technologies and software that provide real-time monitoring, threat information, and incident response capabilities.
APT Defense
When an APT is detected, companies must be able to respond swiftly and effectively to the threat. This includes identifying and isolating compromised systems, controlling malware distribution, and uninstalling malware from affected systems.
APT defense tools and software can assist businesses in accomplishing this by offering incident response and threat hunting skills, as well as the ability to detect, respond to and block malicious activity in real-time.
The Role of Artificial Intelligence in APT Detection and Defense
As the number and complexity of cyber threats grow, many businesses are turning to artificial intelligence (AI) and machine learning (ML) to detect and fight against APTs.
AI and machine learning can assist firms in accomplishing this by providing increased threat detection and response capabilities, as well as the ability to evaluate vast amounts of data in real-time. This can assist enterprises in detecting and responding to APTs before they cause substantial damage.

Top APT Detection and Defense Tools and Software
Some of the best APT Detection Tools
FireEye: FireEye is a threat intelligence and incident response company that offers real-time monitoring and advanced malware analysis.

Symantec: Symantec provides APT detection products such as endpoint protection, network security, and threat intelligence.

Kaspersky: Kaspersky provides sophisticated threat detection and response capabilities, such as real-time monitoring and advanced malware analysis.

Top APT Defense Tools
Cylance: Cylance offers advanced threat defense features such as real-time surveillance and advanced malware analysis.

Carbon Black: Carbon Black provides advanced threat defense capabilities, such as incident response and threat hunting.

McAfee: McAfee offers sophisticated threat defense capabilities such as real-time monitoring and insider threat analysis.

Implementing APT Detection and Defense
Best Practices for APT Detection and Defense
Implementing APT detection and defense technologies and software is an important step in safeguarding your organization from advanced persistent threats. It is critical to follow best practices to maximize the effectiveness of these tools, such as:
Conducting vulnerability assessments and penetration testing on a regular basis
To conduct a vulnerability assessment: a security team would run various automated tools and manual techniques to identify any potential vulnerabilities in the organization's network, systems, and applications. This can be done on a quarterly or semi-annual basis.
To conduct a penetration test: a team of ethical hackers would simulate a real-world attack scenario and attempt to exploit identified vulnerabilities to gain access to the organization's sensitive information. This can be done on an annual basis.
Updating and patching systems and software on a regular basis
The security team would regularly check for updates and patches for all systems and software in use within the organization. This includes operating systems, applications, and third-party software. This process can be automated and scheduled to run daily or weekly.
Putting in place a robust security program that includes personnel training and incident response planning
A robust security program would involve implementing various security controls and policies, such as firewalls, intrusion detection systems, and data encryption. It would also include regular training for all employees on security best practices and incident response procedures.
Monitoring and analyzing network and system records on a regular basis
The security team would use various tools and techniques to continuously monitor and analyze network and system logs for any suspicious activity. This can include automated tools for anomaly detection and manual analysis of log files. This process can be scheduled to run daily or weekly.
Including AI and machine learning in your APT detection and defense plan
AI and machine learning algorithms can be used to automatically detect and respond to advanced persistent threats. This can include using machine learning to analyze network and system logs for patterns of malicious activity, and using AI to automatically respond to detected threats by blocking IP addresses or quarantining infected systems.
How to Implement APT Detection and Defense Tools and Software
Organizations should take the following measures to properly install APT detection and defense techniques and software:
This is how an APT stays alive
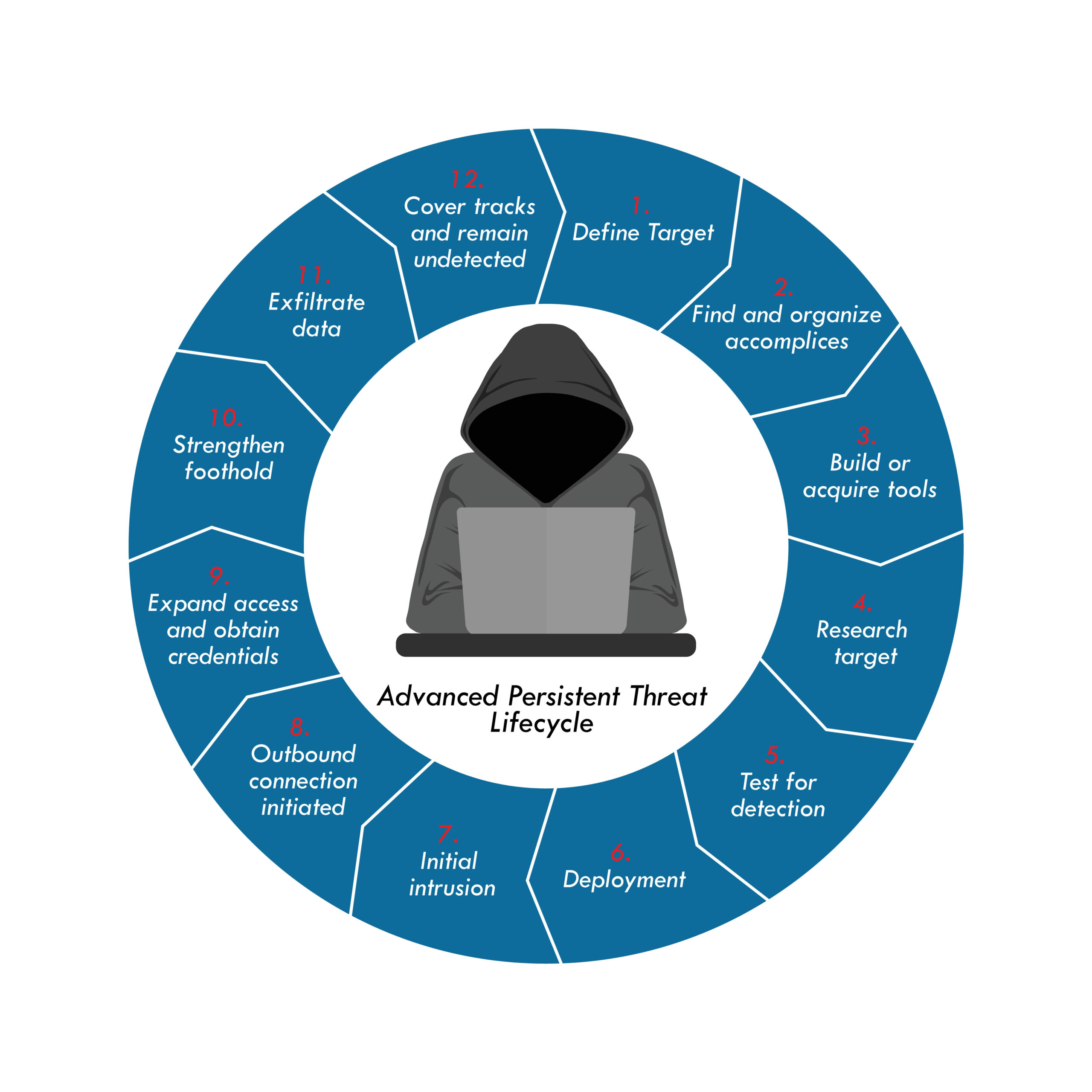
What to keep in mind
APTs are a major concern for businesses of all sizes. To defend against these advanced persistent threats, it is critical to have the proper detection and defense mechanisms in place. Organizations may better detect and fight against APTs and reduce the risk of a disastrous cyberattack by understanding APTs, applying best practices, and employing artificial intelligence and machine learning.
Furthermore, APTs are a sophisticated and complex sort of cyberattack that necessitates a multi-layered approach to detection and protection. Organizations must have visibility into all network traffic and activity, as well as advanced threat detection and defense techniques and software.
Finally, AI and ML can be useful in detecting and combating APTs in real time. Best practices, incident response planning, and routinely monitoring and updating systems can all aid in the prevention of APTs. It is critical to remember that APTs are continually changing, and companies must remain cautious in order to defend themselves.
